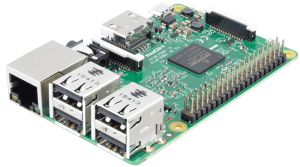
Raspberry Pi Projects NexcloudPi Since I built my Home-Lab Server I have been migrating all my services to Docker Containers. Before that I was looking for a easy and straightforward way to host my files without having to rely on a NAS, since I had already a bunch of 2tb hard drives lying around I […]
Operative Systems Just like you would pick a car brand to drive it around, Operative Systems (OS) have a distinctive way to offer you vehicles to do your tasks. These are Applications or Programs that run on top of these OS. They come of different versions and releases (flavours) according to the end user needs. […]
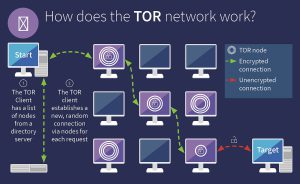
Darknets The darknets which constitute the dark web include small, friend-to-friend peer-to-peer networks, as well as large, popular networks such as Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnet due to its unencrypted nature. The darkweb, commonly referred to as the darknet, […]
A wireless access point (WAP), sometimes known as an access point (AP), is a networking hardware component that enables other Wi-Fi devices to connect to a wired network in computer networking. The AP could be an independent device with a physical connection to a router, but it could also be an essential part of a wireless router.
Electronics Electronics has been for the greatest part of my life a constant hobby and profession, both on the professional plane and when I’m relaxing back at home. I see the world through the eyes of an electronic engineer, no because i plan to se it that way, but because i can’t help to wander […]
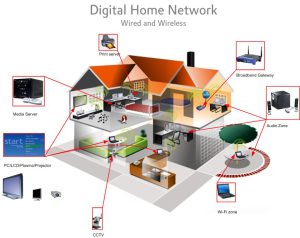
Home Labs Why would you build a Home Lab? Building a home lab can be beneficial for a variety of reasons: Learning and experimenting with new technologies and software Developing and testing new ideas and projects Providing a safe and controlled environment for troubleshooting and problem-solving Saving money on cloud or other hosting costs Improving […]
Before we dive into the nitty-gritty of configuring your network, let’s take a step back and understand why security is so crucial. Here are just a few reasons why:
Data Protection: With sensitive information like personal photos, financial documents, and passwords stored on your devices, it’s vital to keep them safe from unauthorized access.
Identity Theft: Hackers can use your network to gain access to your online accounts, stealing sensitive information and causing identity theft.
Vulnerability Exploitation: Outdated or un-patched software can leave you open to attacks from malicious actors, giving them a foothold in your network.
Protecting sensitive data from unauthorized access or breaches has become a critical concern. Traditional methods of fortifying network defenses often involve building custom hardware firewalls, which can be both time-consuming and costly.
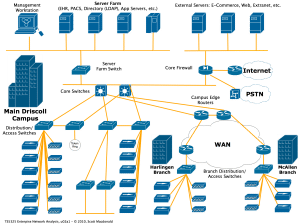
Commercial Networks Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus […]
Cybersecurity Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo. […]