You’ll catch more BotNets with Honey
A honeypot is a type of security system that involves creating a decoy environment, usually on the internet, to detect and analyze cyber attacks. The goal of a honeypot is to identify and learn from malicious activity without compromising the actual network or data.
Benefits of running your own Honeypot:
- Network visibility: A honeypot provides insight into suspicious activity on your local network, allowing you to detect potential security threats earlier than if they were detected by traditional security measures.
- Improved incident response: By monitoring the honeypot’s activity, you can quickly respond to potential security incidents and minimize damage.
- Enhanced threat intelligence: The data collected from the honeypot can be used to improve your organization’s overall security posture, helping you identify vulnerabilities and develop targeted mitigation strategies.
- Reduced false positives: By analyzing the behavior of malicious actors on a honeypot, you can refine your security rules and reduce false positive alerts that might trigger unnecessary responses.
- Cost-effective: Running a honeypot locally eliminates the need for remote monitoring or outsourcing, making it a cost-effective solution for small to medium-sized businesses.
Key advantages of having a honeypot running locally include:
- Real-time visibility: A local honeypot provides immediate visibility into suspicious activity on your network, allowing you to respond quickly.
- Low latency: Since the honeypot is connected directly to your local network, data transmission times are minimal, ensuring accurate analysis of malicious activity.
- Security testing: A local honeypot allows you to test and refine your security measures without exposing sensitive data or disrupting production systems.
- Compliance and regulatory requirements: By monitoring a local honeypot, you can demonstrate compliance with relevant regulations and standards, such as PCI-DSS or HIPAA.
When implementing a local honeypot, consider the following:
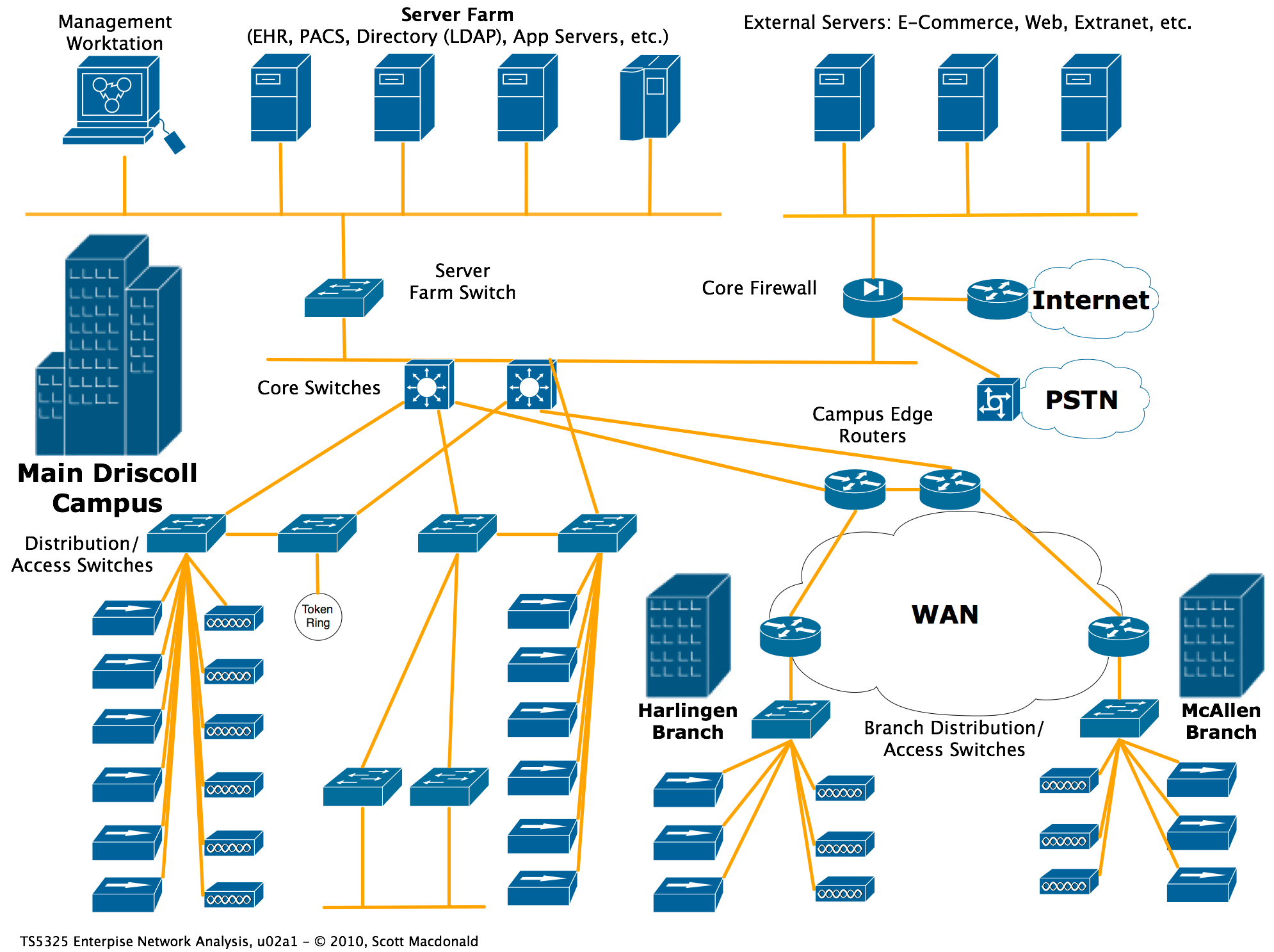
- Choose a suitable environment: Select a network segment that is not critical to your business operations, running in parallel with your ISP modem or before your firewall is the best practice approach.
- Configure carefully: Ensure the honeypot is configured correctly to detect malicious activity without triggering false positives.
- Monitor and analyze data: Regularly review the data generated by the honeypot to refine your security measures and improve incident response.
This way you will gain valuable insights into your network’s security posture, reduce the risk of cyber attacks, and enhance your overall security resilience.
Indiscriminate use of technology
There’s not limit for attackers and data harvesters in the Net when all we do nowadays depends on online services. Attackers will create clever ways to find gaps in our security, these attacks are meticulously crafted to find any vulnerable online device. From private home users to robust Network Systems.
How to deploy your own Honeypot?
Telekom’s t-pot is the easiest way to get started with your Hacker Tracing and Hunting career. A honeypot ready system that you can deploy on multiple systems. And as you may have guess, I will be using Linux to deploy mine, more specifically Ubuntu Sever making sure ssh is included during installation.
Now. I could create a whole article about how to get started and install it, but I’ll leave that to the professionals. You can see and follow the steps from Telekom’s own article here: https://github.security.telekom.com/2024/04/honeypot-tpot-24.04-released.html
To make the long story short. Grab a old computer or an Intel NUC in my case (due to these being low power cost, low maintenance and they are more reliable than a RaspberryPI for high traffic and I/O read and writing)
After choosing your hardware, – you can also go the VM route, but there’s limitations to this- install a fresh copy of Ubuntu Server or the distribution of your choice.
Once Ubuntu is ready, we follow the commands from Telekom’s instructions.
Let’s first make sure curl is installed by entering the following:
curl: $ sudo [apt, dnf, zypper] install curl
Then, we run the t-pot installer as a non-root from $HOME like so:
env bash -c "$(curl -sL https://github.com/telekom-security/tpotce/raw/master/install.sh)"
Or you can follow the official steps from Telekom’s page:
Get and install T-Pot
- Clone the GitHub repository:
$ git clone https://github.com/telekom-security/tpotceor follow the TL;DR and skip this section. - Change into the tpotce/ folder:
$ cd tpotce - Run the installer as non-root:
$ ./install.sh:- ⚠️ Depending on your Linux distribution of choice the installer will:
- Change the SSH port to
tcp/64295 - Disable the DNS Stub Listener to avoid port conflicts with honeypots
- Set SELinux to Monitor Mode
- Set the firewall target for the public zone to ACCEPT
- Add Docker’s repository and install Docker
- Install recommended packages
- Remove packages known to cause issues
- Add the current user to the docker group (allow docker interaction without
sudo) - Add
dpsanddpswaliases (grc docker ps -a,watch -c "grc --colour=on docker ps -a) - Add
la,llandlsaliases (forexa, a improvedlscommand) - Add
mi(formicro, a great alternative toviand / ornano) - Display open ports on the host (compare with T-Pot required ports)
- Add and enable
tpot.serviceto/etc/systemd/systemso T-Pot can automatically start and stop
- Change the SSH port to
- ⚠️ Depending on your Linux distribution of choice the installer will:
- Follow the installer instructions, you will have to enter your user (
sudoorroot) password at least once - Check the installer messages for errors and open ports that might cause port conflicts
- Reboot:
$ sudo reboot
Follow the instructions during installation and configure your environment. By now you should have a working HoneyPot ready to trace and log all the nasty internet traffic that comes your way.
Now you should be able to access your web instance of t-pot
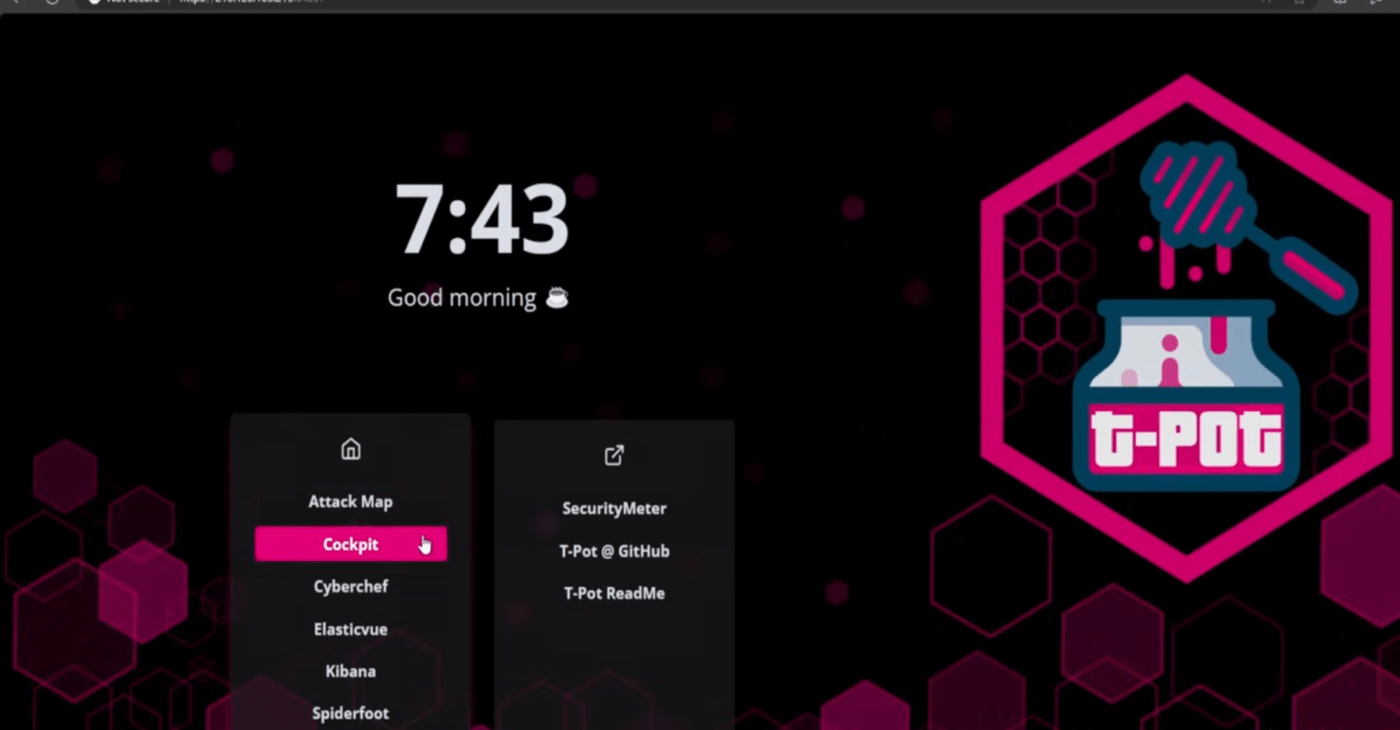
As you can see, getting started with Home Cybersecurity is not hard, configuring the right parameters and knowing what data to look for its what will make you a good cyber analyst and home -or business- network protector.